SOC Services
Secure Your Business with Our SOC Services
Protecting your business from cyber threats is more important than ever. Our SOC services provide you with the comprehensive security solutions you need to keep your data safe and ensure compliance. With our managed SOC services, you can trust that our expert team is monitoring your systems 24/7, ready to take on any threats that come your way.

SOC 1 vs. SOC 2: What’s the Difference?
Understanding the difference between SOC 1 and SOC 2 is key:
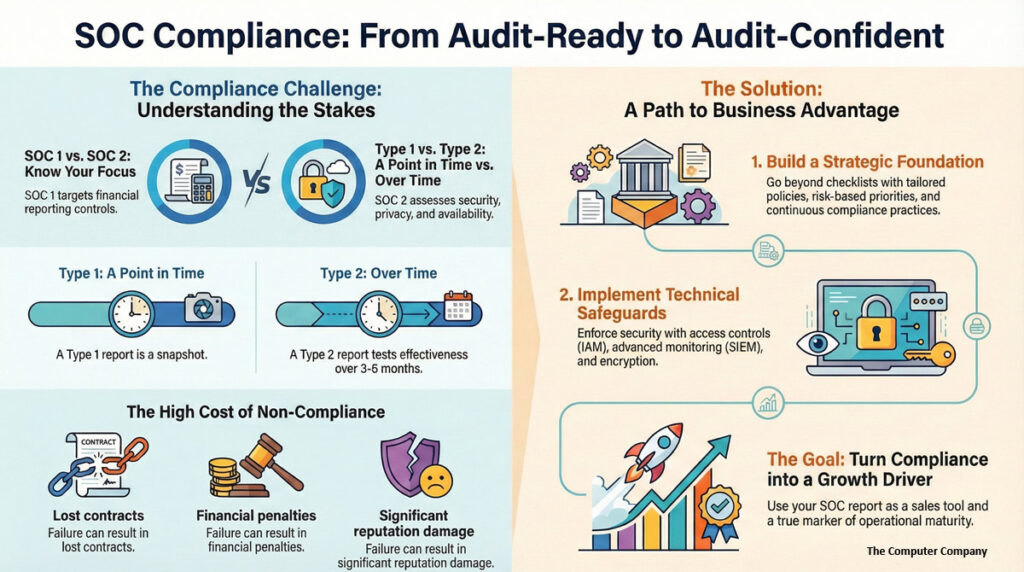
- SOC 1: Focuses on internal controls over financial reporting. It's essential for businesses dealing with financial transactions and client data.
- SOC 2: Centers around data security, privacy, and confidentiality. It’s ideal for tech companies and cloud providers managing sensitive data.
- Type 1 is a snapshot in time, evaluating controls at a specific moment.
- Type 2 looks at controls over 3-6 months, testing their effectiveness over time.
How We Help You Achieve Compliance
Thorough Assessments
We take a deep dive into your systems to find any gaps in your compliance, making sure nothing slips through the cracks.
Tailored Compliance Plans
Every business is different, so we create a compliance strategy that works for your unique needs, making the process as smooth as possible.
24/7 Support with Managed Services
Our managed security operations center offers round-the-clock monitoring and expert support, ensuring you stay compliant without worry.
Learn More With Our Experts
Achieving SOC compliance—whether SOC 1 or SOC 2—is not simply about passing an audit. It’s about creating an environment where controls are embedded into daily operations, producing security, reliability, and trust that extend beyond the report.
Our experts emphasize two equally critical areas:
Strategy & Process
- Choosing the right SOC report:
- SOC 1 validates controls that impact financial reporting.
- SOC 2 assesses IT and operational controls across the Trust Services Criteria (security, availability, processing integrity, confidentiality, and privacy).
Selecting correctly avoids wasted effort and ensures the report speaks to your stakeholders.
- Audit readiness vs. audit resilience:
Many organizations scramble to gather evidence at audit time. We guide companies to adopt continuous compliance practices, embedding control checks, ticketing, and documentation directly into workflows. This creates always-on readiness, lowers costs, and builds long-term trust.
- Tailored policies that scale:
Generic templates often fall apart when scaled. Our experts map SOC controls directly to business processes, technical stacks, and cloud platforms—so what looks good on paper also works in production.
- Risk-based prioritization:
Not all controls carry equal weight. We help leadership identify which SOC criteria have the greatest business, legal, or reputational impact, ensuring resources go to the right areas.
- SOC as a growth driver:
Instead of seeing compliance as a checkbox, organizations use SOC reporting as a sales tool, a partner assurance document, and a baseline for international certifications (like ISO 27001).


Technical Safeguards
- Identity & Access Management (IAM):
Implementing role-based access controls (RBAC), enforcing MFA, and integrating identity solutions (Okta, Azure AD, etc.) ensures access rights match responsibilities and are reviewed continuously.
- Advanced logging & monitoring:
SOC demands evidence, and evidence lives in logs. Centralized SIEM platforms (Splunk, Sentinel, or ELK stack) combined with real-time anomaly detection ensure both audit trail completeness and rapid incident response.
- Encryption & key management:
Strong encryption isn’t enough without proper key lifecycle management. Our experts design systems where keys are rotated, stored in HSMs (hardware security modules), and auditable.
- Change management discipline:
Every system modification—from a code update to a firewall rule—must be logged, tested, and approved. We deploy DevSecOps pipelines that automatically enforce change control while keeping developers agile.
- Availability engineering:
Meeting SOC’s availability criteria requires disaster recovery (DR) and high availability (HA) strategies: geo-redundant backups, load balancing, failover testing, and uptime SLAs. These aren’t just audit checks—they’re survival tools.
- Privacy safeguards:
With SOC 2’s privacy principle, technical measures must align with legal frameworks like GDPR or HIPAA. That means data minimization, anonymization, and strict retention policies built into systems by default.
By aligning governance practices with technical enforcement, The Computer Company helps organizations move from simply “audit-ready” to audit-confident—turning SOC compliance into a business advantage and a true marker of operational maturity.
Consequences of Non-Compliance
Failing to meet SOC compliance standards can hurt your business in several ways:
Lost Contracts
Financial Penalties
Reputation Damage
Why Work with TCC for SOC Compliance Services?
Here’s why businesses choose us for managed SOC services:
Experience
Our team has years of expertise in SOC compliance services across various industries.
Ongoing Support
We don’t just get you compliant; we stay with you, offering continuous monitoring and updates.
Friendly Team
We’re here to help every step of the way, answering questions and providing guidance whenever you need it.
Get SOC Compliant
Let us help you secure your business and meet SOC compliance with ease. Contact us today to learn more about our SOC services and how we can help.
Check Out Our Other IT Compliance Services

HIPAA Compliance Services

CMMC Compliance Services