Multi-Factor Authentication (MFA) or Two-Factor Authentication (2FA) are ways to verify a user’s identity when logging into a digital account. According to a study by Microsoft, it is proven to prevent approximately 99.9% of fraudulent sign-in attempts.
MFA/2FA adds at least one extra requirement before gaining access to an online account. This significantly increases account protection. It may seem like a brief inconvenience by adding another step, but it is more than worth it for the boost in defense. The most common way to add it is to input a code or enable a push notification from your smartphone or other digital device. Our team can easily help your organization enable this great feature. Don’t leave your information vulnerable to bad actors!
Multi-Factor Authentication from Duo
TCC uses Cisco’s Duo, only the best in MFA software. There really is no easier way to use MFA. Designed for the modern workforce and backed by a zero trust philosophy, Duo is a user-friendly, scalable access security platform that keeps any business ahead of ever-changing online threats.
Verify identity in seconds.
Duo is fast and easy for users to set up, and with several available authentication methods, they can choose the one that best fits their workflow.
Protect any application on any device.
Set up new users and support new devices at any time, and protect new applications almost instantly — without impacting legacy systems.
Easily deploy in any environment.
Duo can be added to any existing environment or platform, and its self-enrollment feature makes it easy for users to get set up.
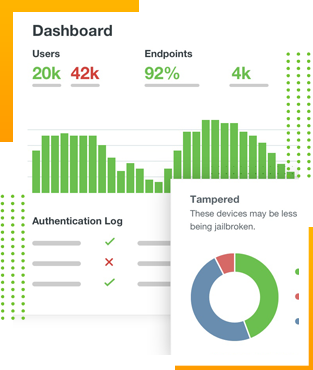
Modern, Effective Multi-Factor Authentication
With an intuitive user-friendly interface, robust administrative dashboard, detailed reporting, and an always-up-to-date cloud-based model, MFA couldn’t be easier to manage. So when it comes to protecting your information, 2FA is here to stay. But how exactly do you find a solution that works for both your end users and your organization’s security policies?
That’s where we can help. Our experienced team can walk you through some of the key areas of differentiation between two-factor authentication solutions and provide concrete criteria for evaluating technologies and vendors.
